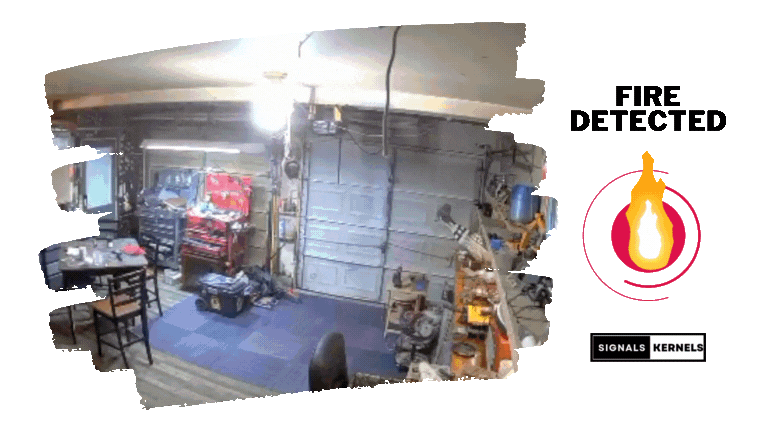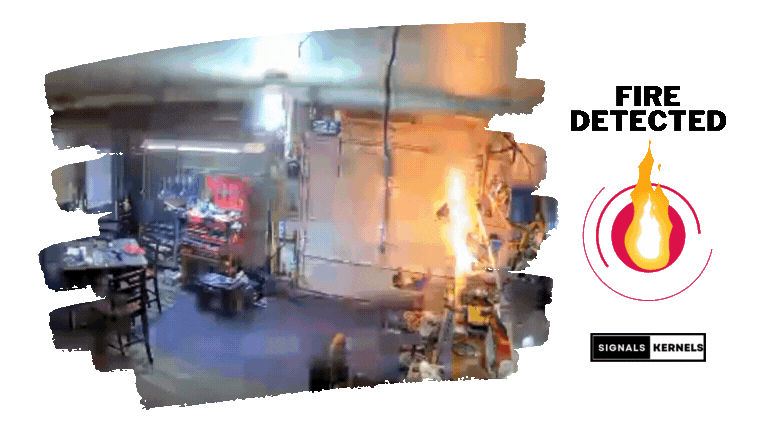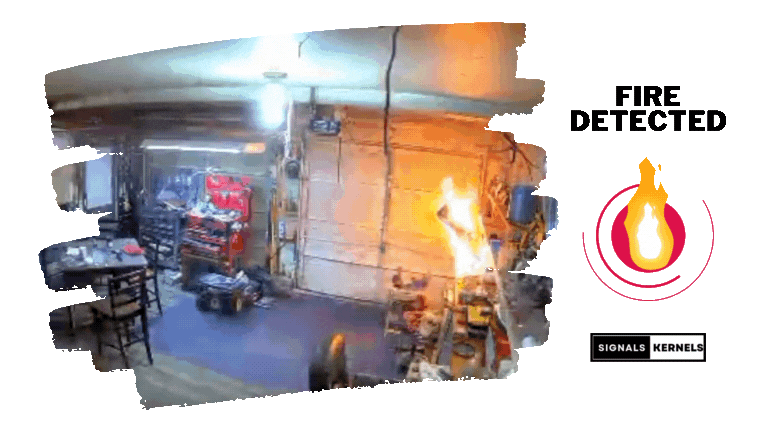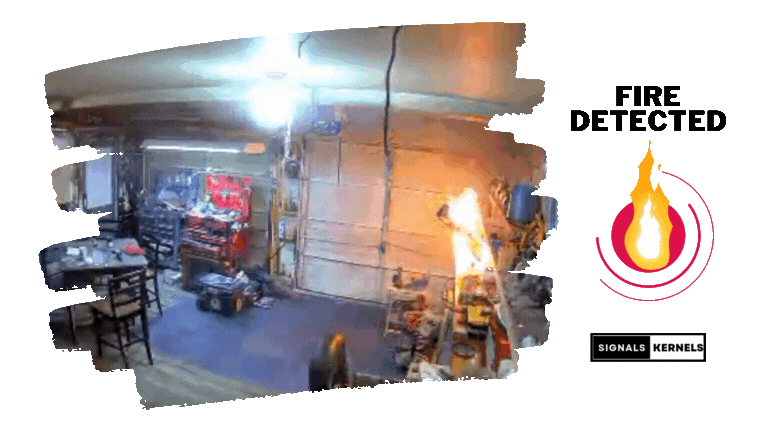
Motion Detection
Detects movement to identify potential security breaches and employs advanced algorithms to minimize false alarms.
- Intelligent Motion Sensing: Customizable schedules for after-hours.
- Smart Notifications: Real-time alerts with configurable priority.
 HARIS
HARIS